Over the last year or so, we have seen “random” cases, where one delegate admin suddenly was unable to log into one specific Business Central tenant on the cloud. The usual remedy is that we create extra users in our AAD that are only used for delegate admin stuff.
Then last night, in a related discussion on Twitter, Dmitry from Microsoft dropped this bomb:
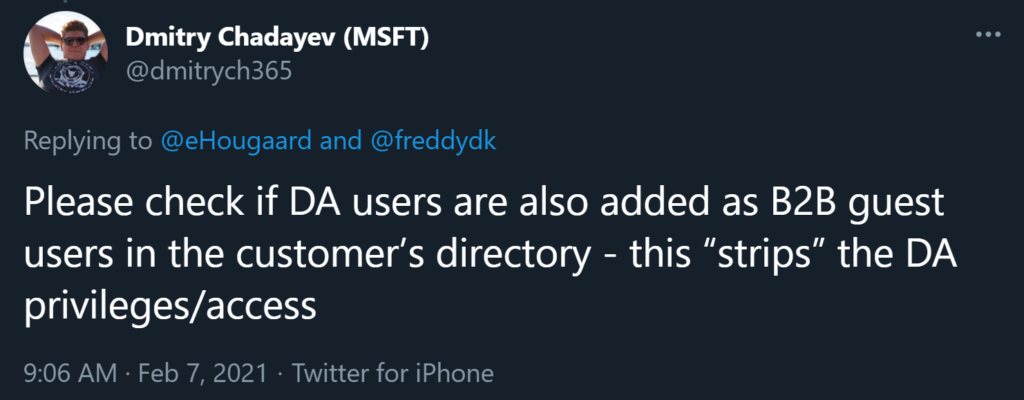
And for sure, when dealing with another tenant, your account can become a Guest Account in the client’s AAD. (Like joining the customer’s Teams organization, or if stuff is shared to you).
So I deleted the “Erik guest” from Guest Users(*) in a tenant where I have been locked out for quite a while.
And….

My account can now both deploy to sandboxes and access the tenant again!
This is kind of weird and problematic to need multiple accounts, so I hope that Microsoft will remove this restriction.
(*) Access the AAD from admin.microsoft.com or from the Azure Portal of the tenant.